Uplink: Hacker Elite
Windows - 2001
Also released on: Mac - Linux
Description of Uplink: Hacker Elite
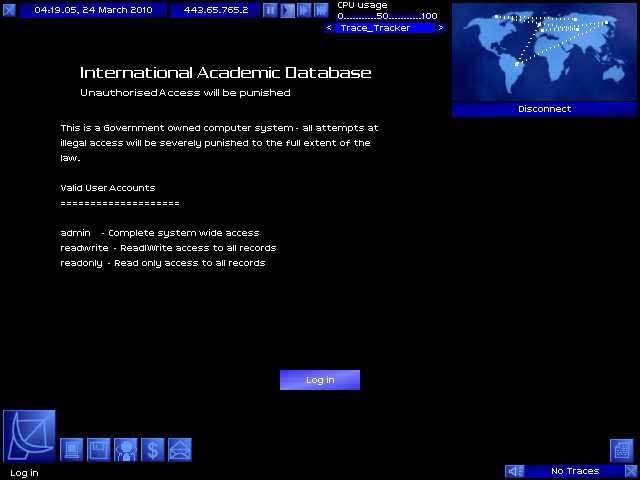
In March of 2010, you decide to embark on a new career. Logging into the Uplink Corporation Public Access Server, you sign in, take out a loan for 3,000 credits from the Uplink Corporation Bank, and go into business as a hacker. The Uplink Corporation provides you with a basic Gateway system through which you connect to the Net, banking services, shops in which to buy new and better hardware, software, and gateways... and contact with those desiring your services.
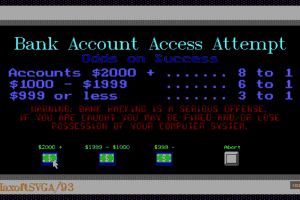
Please be aware that Uplink will NOT teach you how to conduct real-world hacking. It is not a manual for computer crime, nor does it require you to write programs. Uplink presents Hollywood hacking in a near-future cyberpunk atmosphere: there are enough things reminiscent of the real world to allow immersion, but Introversion removed the drudgery. You buy your software, whether a password cracker or a program to break an Elliptic Curve Cypher, and the skill lies in your strategies for the deployment of these tools. In the process, Uplink is one of the most innovative games we've seen in years. It doesn't present hacking as a 3D shooter in a virtual space, or as part of a wider adventure game, as every other cyberpunk or hacking game has. Instead, it presents a radically simplified version of real-world hacking, in which the player needs to find passwords through brute force and some critical actions can only be achieved via a Unix console.
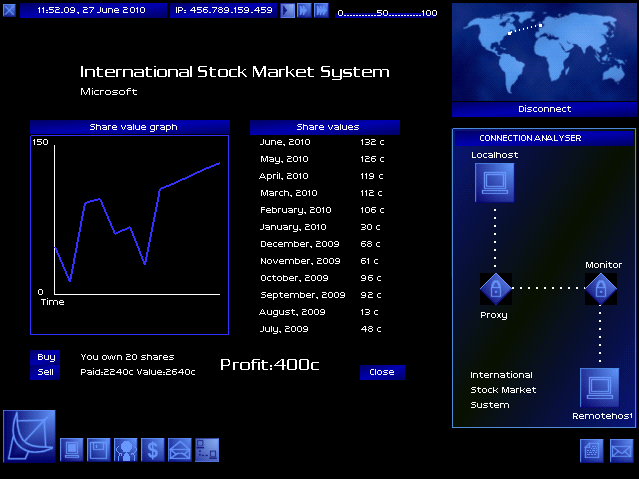
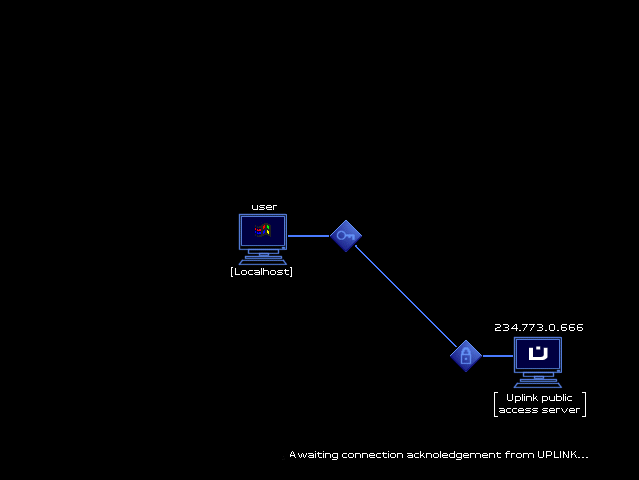
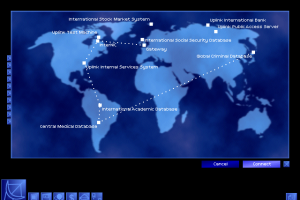
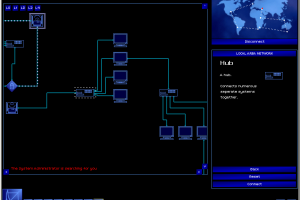
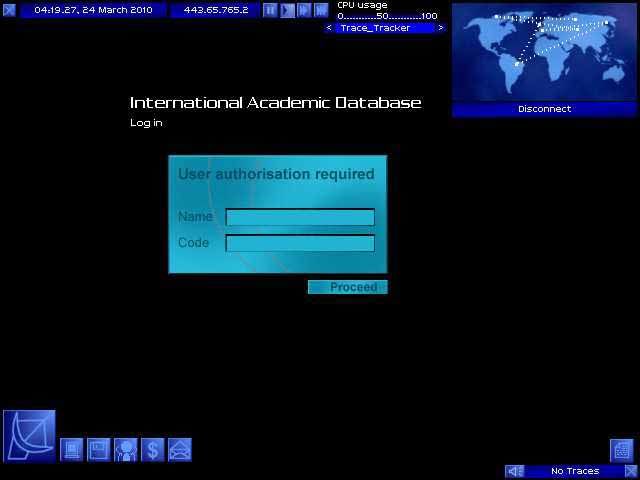
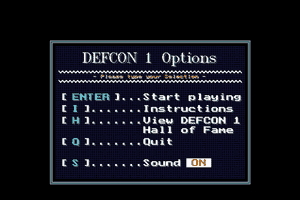
So, armed with your nifty new password breaker, you choose a path of bounces to a system, set the Password Breaker's CPU priority to maximum, and set it to working out the admin password. The rapid flurry of attempts to log into the admin account sets off alarms, and the system you are hacking defends itself by both active and passive tracing. Active traces provide a timer for the duration of your intrusion: once the active trace finds your Gateway, you've been caught.
You can run a "Trace Tracker" program to warn you of the progress of this trace, and you can increase the time you have by bouncing through more servers (especially if you have admin access on them). Even so, the countdown timer almost always provides a real sense of urgency, and later in the game, when you have sophisticated programs to avoid triggering an active trace, the avoidance lends a real air of stealthy entry. Following behind the active trace is the passive trace, slower but surer, as security at the system you hacked into traces back through your bounce route, seeking your home system. Later in the game, the person backtracking a hack may be you, hired to find another hacker.
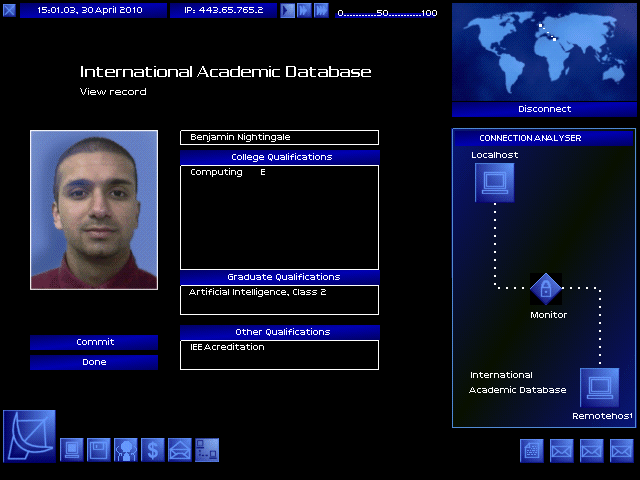
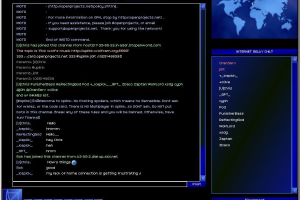
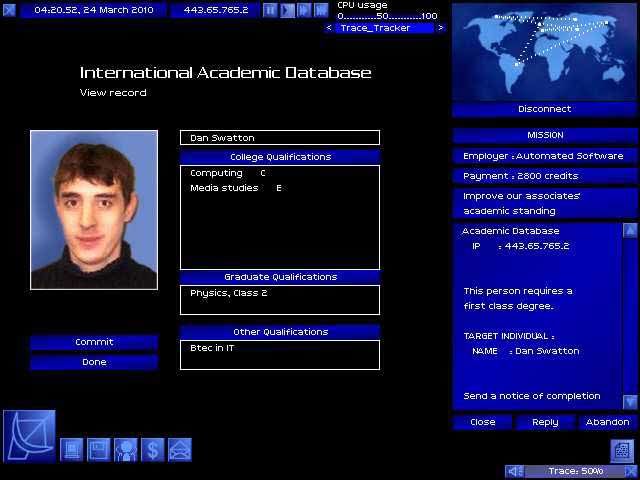
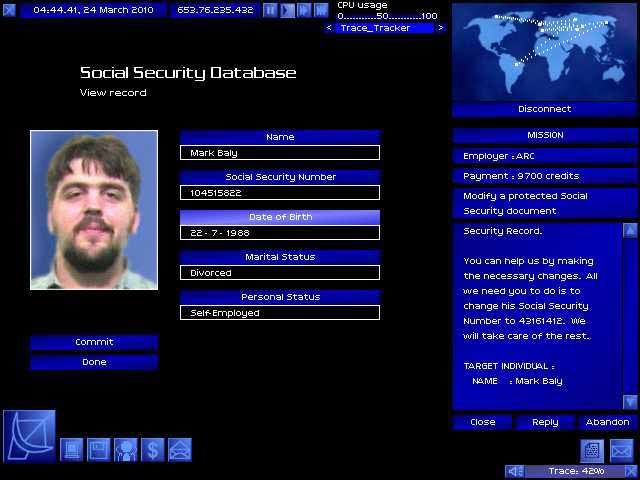
To defeat the passive trace, you need to destroy the log files on at least one of the systems you bounced through. Thus, even the simplest hacking job requires at least two pieces of hacking: one to do the job, and another to cover your tracks. As you accomplish missions, your rating within the Uplink Corporation increases and more difficult missions become open to you. Initially, the missions tend to be simple "copy this file" or "delete this file" jobs. Later missions include altering Social Security and criminal records, robbing banks, framing other hackers, and running a passive trace on another hacker.
These later missions often become quite complex, requiring you to do quite a bit of groundwork in preparation for the hacks in which you accomplish the mission, and the complex hacks themselves require a fair amount of orchestration. Best of all, the hacking works very well in providing a sense of tension, required skill, and accomplishment. Hacking is the centerpiece of the game, and Uplinkhacking is addictive in that wonderful, "Is the sun rising already?" way.
On a philosophical note, a friend pointed out that Uplink is an example of a "total" fiction: a fiction that merges seamlessly with the real world. If the world presented in Uplink were real, and players were really Uplink agents, then nothing of what you see in the game or your computer room would be different. As a result, there's not the break in immersion that you get in most games where the edge of the monitor is a break with the gameworld. Furthermore, while the graphics seem spartan, they also feel perfectly suited to the game. Uplink won't show off your graphics card, but, staying within the game fiction, wouldn't you rather have your processing power making your password breaker run faster than have a pretty 3D interface? On the other hand, there's the minor gripe that the number of pictures in the various government databases isn't enough to prevent them from being repetitive.
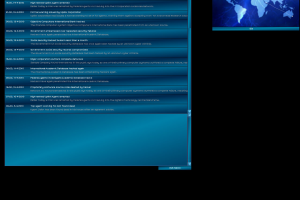
All of this takes place inside a very open framework. You look through the missions offered and choose which ones you want to try. If you'd prefer, you can ignore them all and let time advance until you find one you like. Most of the missions have nothing to do with any form of a plot, so much of the game revolves around the time-honoured dynamic of "do missions to buy better equipment to do harder missions." This dynamic works well in other games, and it works well here, too. Moreover, after you've gotten a fair distance into the game, there is a wider plot that you can choose to become involved in on either of two sides, seeking to save or destroy the Internet.
There are a few bugs in the code, however. Uplink uses OpenGL, which can cause problems with Voodoo cards, and a second monitor will slow the game down greatly unless you disable it. The other potential show-stopper is periodic crashes, which the v1.01 patch helps with, but doesn't entirely stop. In lesser gripes, the Internet node map can get awfully crowded, so it's a shame the game cannot be run in a higher resolution than 640x480. The game includes a step-by-step tutorial for basic hacking, which is good, but you must follow the tutorials in lock-step or the onscreen instructions won't advance. (In further evidence of ensuring there are no breaks in the game fiction, the tutorial is literally a program in your gateway system's memory banks.) Another problem is that some mission descriptions are a bit vague on exactly what you need to do to succeed.
Uplink isn't for everyone; some players may be turned off by the amorality of the actions the player is expected to perform, because it simulates criminal acts, including the destruction of billions of credits of data and ruining people's lives. The game does not put you in a heroic good-guy role, which is perfectly in keeping with the cyberpunk genre but may prove unsettling.
Overall, Uplink belongs in the pantheon of great games. It may not have the ad campaign of the more famous titles released this season, but it delivers all the immersion, innovation, and entertainment you can ask for.
Review By GamesDomain
External links
Captures and Snapshots
Comments and reviews
There is no comment nor review for this game at the moment.
Write a comment
Share your gamer memories, give useful links or comment anything you'd like. This game is no longer abandonware, we won't put it back online.
Buy Uplink: Hacker Elite
Uplink: Hacker Elite is available for a small price on the following website, and is no longer abandonware. GOG.com provides the best release and does not include DRM, please buy from them! You can read our online store guide .
Other Releases
Uplink: Hacker Elite was also released on the following systems:
Mac
- Year: 2003
- Publisher: Ambrosia Software, Inc., Introversion Software Limited
- Developer: Introversion Software Limited
Linux
- Year: 2003
- Publisher: Introversion Software Limited, Purple Hills, Strategy First, Inc.
- Developer: Introversion Software Limited
Similar games
Fellow retro gamers also downloaded these games: